If you read nothing else this month, read Mick Bauer’s article about securing your name server.
If you read nothing else this month, read Mick Bauer’s article about securing your name server (see page 92). Vulnerabilities in old versions of the name server software BIND are the number-one security problem on Linux systems. If you don’t want to wake up to a mailbox full of complaints about script kiddies conducting denial-of-service attacks from your system, do what Mick says. Now. You can read the rest of this any time.
You’re back? Good. Now that your name server is secure, we have some other security HOWTO articles for you to read in this issue, too. Your mail server might be another target for an attack. Mick has another helpful security measure: put a SMTP gateway between the outside world and the feature-rich server where the user’s mail lives. Especially if you have to support a proprietary mail server and can’t count on security fixes, this kind of “bastion host” for mail is better than relying on a firewall that has only a minimal understanding of what mail is.
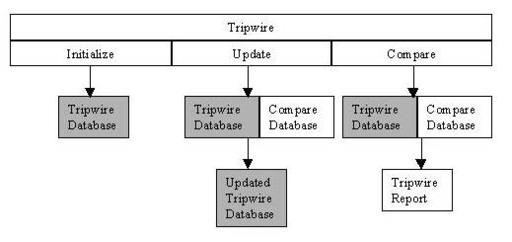
Finally, intrusion detection won’t keep attackers out, but it will let you track them down. And setting up intrusion detection tools doesn’t mean you have to fall for some proprietary vendor’s story. See “Open- Source Intrusion-Detection Tools for Linux” for software that puts you in control.
The big news in security is the expiration of the RSA patent, which, along with the U.S. government’s relaxation of export controls, means we can use open-source security tools such as OpenSSL everywhere. No more paying tribute to the RSA bandits to use their patent. That’s great news, and we expect the Linux distributions to start integrating strong crypto everywhere.
With RSA and the government out of the way, what’s stopping Linux from getting seriously secure? Nothing but us, any more. As Linux Journal moves into the post-excuses world of crypto everywhere, we’ll be running regular articles on how to clean up your act, security-wise, and holding vendors to tighter standards of security cluefulness. We want our readers to learn about security from this magazine, not from a pager in the middle of the night.
Peace and Linux.
 Linux, Linux OS, Free Linux Operating System, Linux India Linux, Linux OS,Free Linux Operating System,Linux India supports Linux users in India, Free Software on Linux OS, Linux India helps to growth Linux OS in India
Linux, Linux OS, Free Linux Operating System, Linux India Linux, Linux OS,Free Linux Operating System,Linux India supports Linux users in India, Free Software on Linux OS, Linux India helps to growth Linux OS in India