Jason Schumaker Issue #79, November 2000 Can’t afford Don Marti’s “Ultimate” Linux box? Well, read on—Jasonw outlines options for the economically challenged. Don Marti’s a big spender. In his article, “Building the Ultimate Linux Workstation”, he waxes technical, recommending various components needed to build the mother of all Linux workstations (see page 80). He has little regard for expense, and ...
Read More »Blog Page
AMD’s Duron Processor
Don Marti Issue #79, November 2000 A $70 CPU may be all that you need for responsive word processing, photo editing, and coding. We take a first look at AMD’s Duron, an excellent choice for midrange desktop Linux machines. I have seen the future of desktop Linux systems, and its name is Duron. A lot ...
Read More »Building the Ultimate Linux Workstation
Don Marti Issue #79, November 2000 We went to hardware experts to find the best and fastest components for building your own Linux workstation. Here’s how to make a responsive system with high-performance 3-D, fast disk, lush sound and the little things to keep it trouble-free. In 1996, Eric Raymond wrote a popular article for LJ called “Building the Perfect ...
Read More »Focus: Hardware
Don Marti Issue #79, November 2000 If you’re on a shopping trip for PC hardware, and you come across this magazine in your favorite computer store, read the hardware articles before you hit the aisles. A man went to the doctor and said, “Doctor, it hurts when I do this.” “Well, don’t do that, then,” said the doctor. Simple but ...
Read More »Booting Problem
Best of Technical Support Various Issue #78, October 2000 Our experts answer your technical questions. Dependencies and Libraries Recently, I downloaded a Linux application and when I tried installing it, I encountered an “unsatisfied dependencies” error message in the package manager. Where do you go for missing Linux libraries and how do you install them? —Kelvin L. Barnes, Kelvin.Barnes@worldnet.att.net If ...
Read More »securing your name server
Don Marti Issue #78, October 2000 If you read nothing else this month, read Mick Bauer’s article about securing your name server. If you read nothing else this month, read Mick Bauer’s article about securing your name server (see page 92). Vulnerabilities in old versions of the name server software BIND are the number-one security problem on Linux systems. If ...
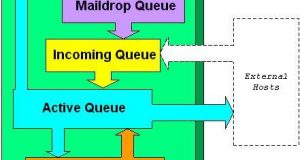
Read More »Using Postfix for Secure SMTP Gateways
Mick Bauer Brenno de Winter Issue #78, October 2000 Improve your site’s e-mail hygiene and make life difficult for spammers and hackers. E-mail is easily the most popular and important Internet service today, which has made it a popular target of cyber-criminals and spam-happy miscreants. Adding to the problem is the inescapable reality that configuring sendmail, the most commonly used ...
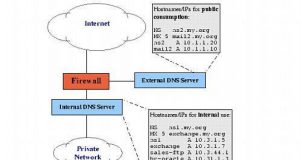
Read More »Securing DNS and BIND
Michael D. Bauer Issue #78, October 2000 Decreasing the vulnerability of your DNS server is largely a matter of staying current and private. In the SANS Institute’s recent consensus document “How to Eliminate the Ten Most Critical Internet Security Threats” (www.sans.org/topten.htm), the number-one category of vulnerabilities reported by survey participants was BIND weaknesses. BIND, of course, is the open-source software ...
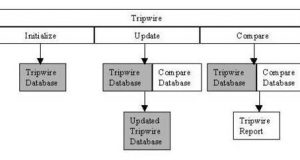
Read More »Open-Source Intrusion-Detection Tools for Linux
Bobby S. Wen Issue #78, October 2000 Armed with Linux and open-source tools, you can even keep an ISP secure. As an ISP, we are the most vulnerable to attack because of the open nature of our networks. Unlike corporate networks, which can limit access, and can backtrack users, we have to continuously monitor for attacks and, more importantly, successful ...
Read More »Mounting NFS
Best of Technical Support Various Issue #65, September 1999 Our experts answer your technical questions. Adding New Users I am having extreme difficulty adding users on Red Hat 5.1. I’ve used various methods to add them to my system via the adduser command and through various X control-panel programs. When I add them, everything seems to go well, and they ...
Read More » Linux, Linux OS, Free Linux Operating System, Linux India Linux, Linux OS,Free Linux Operating System,Linux India supports Linux users in India, Free Software on Linux OS, Linux India helps to growth Linux OS in India
Linux, Linux OS, Free Linux Operating System, Linux India Linux, Linux OS,Free Linux Operating System,Linux India supports Linux users in India, Free Software on Linux OS, Linux India helps to growth Linux OS in India